Top Guidelines Of Data Security Services
Initially, there is actually the legal as well as moral obligation that firms possess to shield their user and client records coming from falling under the inappropriate possessions. Monetary firms, as an example, may go through the Payment Memory Card Business Information Surveillance Standard (PCI DSS) that forces business to take all affordable solutions to defend customer information.
If you don't take information protection truly, your track record could be completely damaged in the occasion of an advertised, prominent breach or even hack. Certainly not to state the economic and also logistical repercussions if a record violation occurs. You'll need to hang around as well as money to analyze and also repair the damages, and also calculate which service methods neglected as well as what needs to become improved.
The Only Guide to Data Security Services
Today, sizable volumes of records are seen as a responsibility coming from a surveillance viewpoint. The more data you possess, the higher the amount of targets for cyberpunks.
There are actually many steps, approaches, and best process that can easily aid minimize the possibilities of a data breach, reduction, and exposure. One typical records administration mistake is placing sensitive documents on a common or even open travel obtainable to the whole company. data security services. You'll want to remove this technique, placing sensitive data in to safely and securely quarantined locations.
Excessively permissive actions is actually one more typical misstep, where additional people possess accessibility to records than is needed. A convoluted web of short-term access as well as authorizations rapidly occurs, with individuals having access to records that they should not. Restriction over-permissioning by utilizing software program that accounts consumer behavior and automatically positions proper behavior-based approvals via an entitlement customer review. Really good data security is everything about planning ahead.
Getting My Data Security Services To Work
Besides the best innovations as well as cyber care ideal methods, your company needs to additionally possess the observing organization procedure abilities and options to make certain ongoing records safety It is actually vital to understand where each one of your information resides at any offered time - data security services. This includes information you're presently using along with data that must be deleted or retired.
One of the most significant dangers to records surveillance is actually interior staffs gaining access to data that they should not. You'll require to track individual accessibility to make certain just the right folks are accessing the very most sensitive information.
Records safety and security is actually a teamwork that need to be tackled coming from all angles. Through knowing what data safety and security is actually and also the procedures you may require to improve it you'll lessen the risk of violations, hacks, or unexpected data reduction.
Data Security Services Things To Know Before You Get This
Really few firms along with workers have actually certainly not adapted swiftly to this brand new, typically remote functioning garden. COVID has actually given rise to a better requirement for distant working and also much more strict records safety than before.
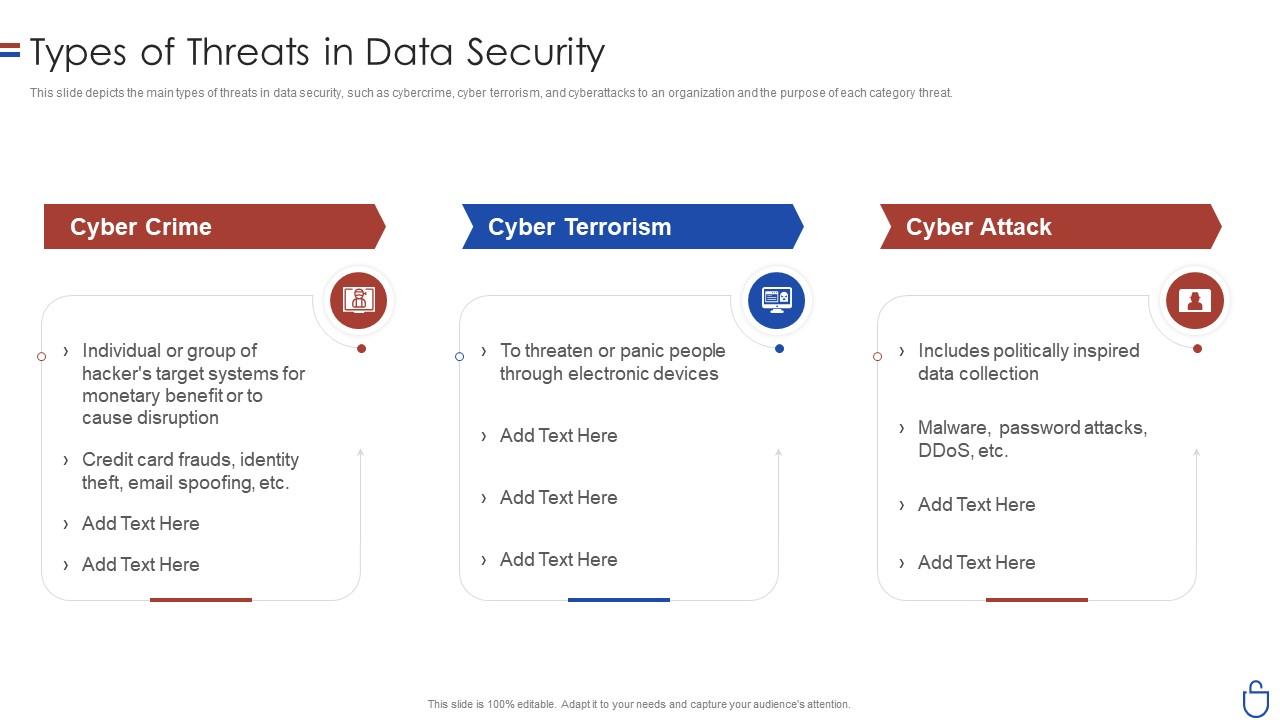
Details like worker and consumer information and also intellectual property are leading targets for hackers. The folks and technology made use of to protect this information are vital to guarding your business's credibility as well as lower series.
The Basic Principles Of Data Security Services
In addition, others will definitely move to a hybrid model, along with some positions in workplace and also others carrying on to be actually remote, and also even more others functioning remote part-time. The concern is actually right now exactly how to defend the provider's data while promoting performance and partnership. The job of technology in the work environment is primarily to assist employees.
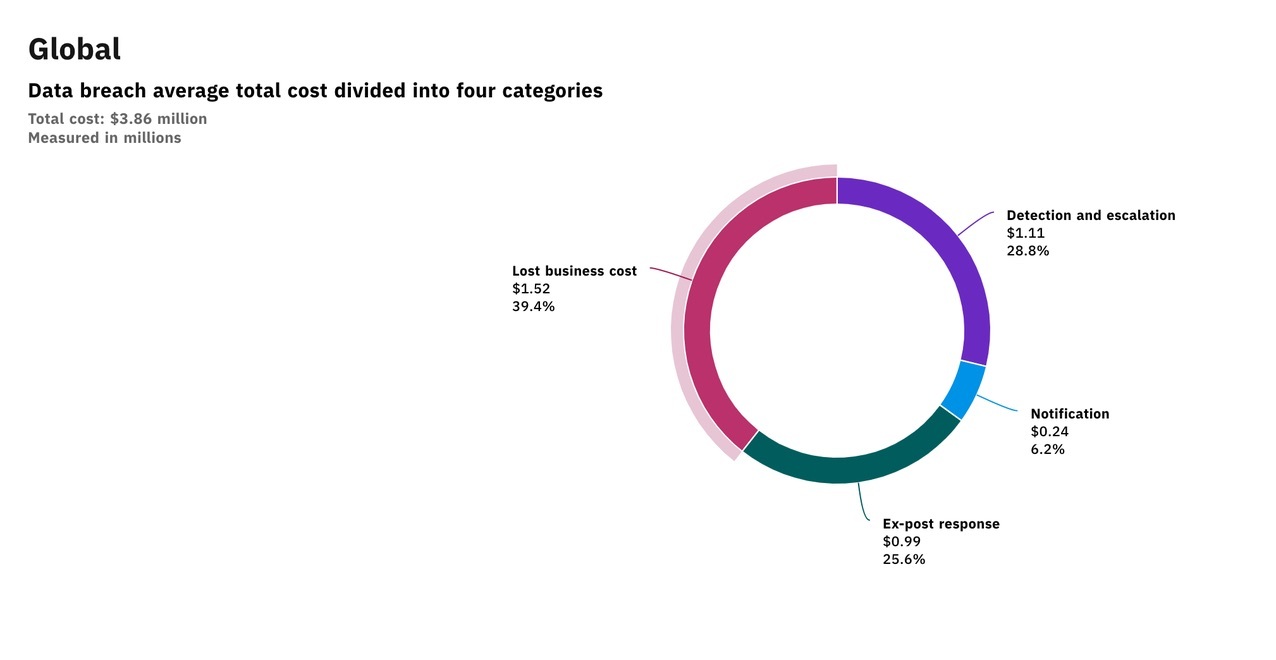
Cyber safety and security and organization continuity are frequently thought about totally different aspects of a service. Alternatively, changes in the online risk landscape show business that this is a factor that our team should closely review. Instead of straining surveillance procedures focuses along with inaccurate tops, there requires to be individual focus as well as reliable computerization.
Some Known Questions About Data Security Services.
Handling numerous elements that carry out certainly not interact with each other is an inefficient task. Covering troubles individually can easily frequently produce more holes than which you started. Cyberpunks recognize this original site and also make use of it every odds they obtain. Furthermore, not maintaining upgraded apps triggers added security concerns.
In order to attain this, a number of people require access to the same records. Creating democratization of data comes along with threat.







